What is E-Discovery? Part 2 - Identification, Preservation, Collection
 This is the second post in a series of five providing a roadmap for you to develop your own e-discovery plan. The first post provided an introduction to e-discovery and the E-Discovery Reference Model, which provides the framework for this blog series.
This is the second post in a series of five providing a roadmap for you to develop your own e-discovery plan. The first post provided an introduction to e-discovery and the E-Discovery Reference Model, which provides the framework for this blog series.
The first phase of your e-discovery plan involves figuring out what documents you need to get and going to get them. Just like any other case, you need documents directly related to the claims and defenses and you need documents requested in discovery. Today’s post will cover the Identification, Preservation, and Collection stages of the E-Discovery Reference Model.
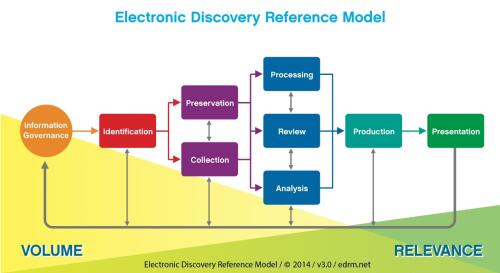
Identification
Your first step will be to identify who the most relevant custodians are and where their data is kept. A custodian is simply a person/place with relevant data. Keep in mind that a custodian could be a network server or drive! The best way to determine where relevant data resides is to ask your client. Ask about computers, servers, mobile devices, backup tapes, paper files, and more. If you need help developing a list of questions, the EDRM can get you started. The Lawyerist Blog also devoted an entire post to the client interview stage and provides a sample questionnaire.
Preservation
While asking your client about the location of their relevant data, you’ll also want to ask about your client’s information governance policies. This will include, for example, their e-mail deletion policies, what they do with an employee’s computer/data when they depart the company, and whether they overwrite back up tapes. You can find sample questions related to records management on the EDRM site. Be aware that your client’s information governance policies may be at odds with their duty to preserve (they may have to suspend their e-mail deletion or stop overwriting their back up tapes).
Next you’ll need a litigation hold memo informing your client in writing of their duty to preserve relevant documents. This memo should be distributed, by your client, to relevant custodians and IT staff, and will serve to remind them not to delete electronic documents or shred paper documents related to the litigation. A litigation hold memo can be in the form of a memo, a letter, or an e-mail. Several samples can be found on the internet by Googling the term “litigation hold memo.” If the litigation spans many years, don’t be afraid to follow up with your client; sometimes people forget and employees turn over.
Collection
There are several different options for collection. The EDRM evaluates these different methods and lays out the pros and cons of each. We will focus on the difference between a forensic and a non-forensic collection.
A forensic collection is when you preserve all aspects of the document’s metadata. This will likely involve a vendor and/or special processing software that copies the entire hard drive or targeted data without altering the metadata.
A non-forensic collection is when you do not preserve all aspects of the document’s metadata. Here are some examples:
- Your client copies loose e-documents to a flash drive or uploads them to the cloud. At the least, this alters the dates last modified, dates last accessed, and creation dates.
- Your client forwards you e-mails. This significantly altering the email’s metadata – the sender, the recipient, the date sent, and the subject line are all changed.
Additionally, non-forensic collections may omit folder paths and other custodial information. This metadata can be very helpful for you and is worth preserving!
Why does identification, preservation, and collection matter? The failure to identify, collect, and preserve relevant electronic data can lead to spoliation charges, monetary sanctions, and even an adverse inference instruction (because the evidence was not preserved, the jury may infer that the evidence would have been unfavorable to the party responsible for its destruction). You can also lose valuable, helpful data that helps you prove your case!
The next post will address Processing and Review, and will help you figure out what to do with all the data you’ve collected.




